Recently I wanted to relive Oblivion but getting it up and running on my current Kubuntu setup was a struggle. I realize Lutris is a great option for installing games on Linux. However, I have had mixed luck with it. It caused the strangest issue with my external displays where any app that used OpenGL. Any time one of these apps would open, my external displays would get disconnected… Super strange, but when I uninstalled Lutris the issue stopped. Due to this, I figured out how to Install Bethesda Launcher with with Wine and Winetricks. Then after that was up and running I was having issues actually installing Oblivion. That’s when I found this helper script that when you run it allows you to install games inside Bethesda launcher. After that I ran into an issue where after a few minutes of playing Oblivion it would crash. Its due to codecs missing and after installing gstreamer1.0-plugins-bad:i386 and gstreamer1.0-plugins-ugly:i386 the game stopped crashing. Here are the steps I followed to Install Bethesda Launcher with wine and Oblivion on Linux.
Installing Wine from WineHQ and Winetricks
I followed the guide from WinHQ’s website here. Basically you do these few commands:
Enable 32-bit (i386) applications in Apt
sudo dpkg --add-architecture i386 Download and install key
wget -nc https://dl.winehq.org/wine-builds/winehq.key
sudo apt-key add winehq.keyInstall repository for Ubuntu 20.04
sudo add-apt-repository 'deb https://dl.winehq.org/wine-builds/ubuntu/ focal main'Install stable version of WineHQ
sudo apt update && sudo apt install --install-recommends winehq-stableThis install takes a little while but will add all the components we need. The next thing we need is winetricks. Winetricks will be used to install missing windows components needed for the game to run. Install winetricks:
sudo apt install winetricksAdd Needed components from winetricks
Now if we tried to install Bethesda launcher it will install but, when you open it, text will be blank. To avoid this we need to install a couple things in winetricks:
Open winetricks with this command. It’s important that you DO NOT use sudo here:
winetricks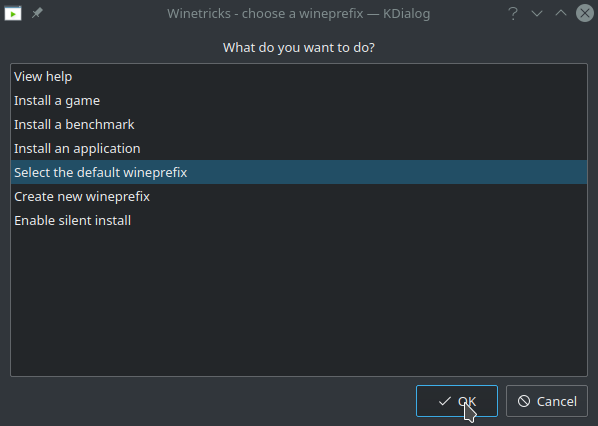
The main winetricks window will open. Click “Select the default wineprefix” and then click OK. In the next screen select “Install a Windows DDL or component” and click OK.
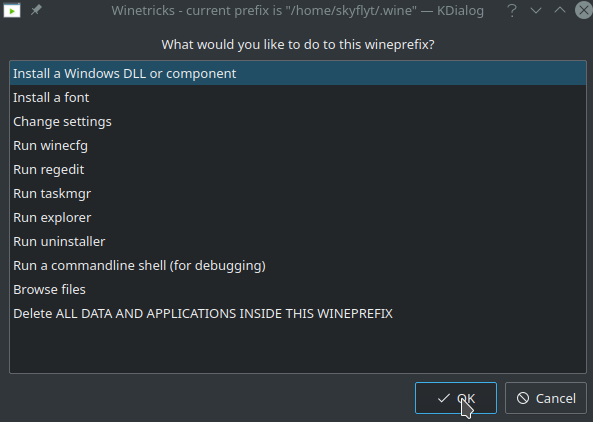
Now scroll down and select vcrun2008 and click ok. This will install the x86 and x64 version of vcrun2008. When that is complete go back into “Install a Windows DLL or component” and this time install vcrun2012. Once that is complete select “Install a Font.” In this menu, select corefonts and click OK. This install takes a bit longer than the others. You will keep getting pop up boxes, just keep clicking ok until it all completes. You can now close winetricks.
Install MPG123 codec support
As I mentioned above, if you don’t add MPG123 support Oblivion will crash after a few minutes. To get this support you need to install a couple x86 gstreamer packages; gstreamer1.0-plugins-bad:i386 and gstreamer1.0-plugins-ugly:i386. To install these run:
sudo apt install gstreamer1.0-plugins-bad:i386 && sudo apt install gstreamer1.0-plugins-ugly:i386Now that we have taken care of the prereqs lets install Bethesda Launcher.
Installing Bethesda Launcher
Now we can do the actual installs. First we need to get the latest bethesda launcher install from here. Now open terminal and path to the download. Run this command to start the install:
wine BethesdaNetLauncher_Setup.exeThis will launch the installer. Go through it and will will install the launcher and open it. Now you can sign in and we can install Oblivion!
Installing Oblivion
Before we can install anything with the Bethesda launcher we need to get the helper script. Download this script and put it in the same directory as the Bethesda Launcher. For me the location is here: /home/user/.wine/drive_c/Program\ Files\ \(x86\)/Bethesda.net\ Launcher/. Once that file is created make sure its executable by running:
chmod +x helper.shnow run the script:
./helper.sh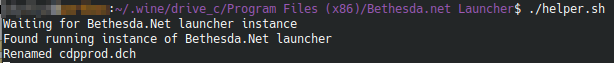
If the script runs correctly you should see that it renames a file. If that all looks good head back over to the launcher and install Oblivion (or any other game you want to buy). The install will complete and you can click “Play” to launch Oblivion right from the launcher.
You may not want to wait for the launcher to open everytime you want to play so here is a launcher script you can create. This will launch Oblivion from terminal without waiting for the launcher to open. I got this from here. Create a file with these contents:
#!/bin/sh
# This script disables all the text output for Wine
# debugging for improved performance.
export WINEDEBUG=fixme-all,err-all,warn-all,trace-all
OBLIVION_DIR=/opt/games/Windows/Oblivion
cd "${OBLIVION_DIR}"
wine OblivionLauncher.exeYou need to change the OBLIVION_DIR line to have to path to your Oblivion install. My completed file looks like this:
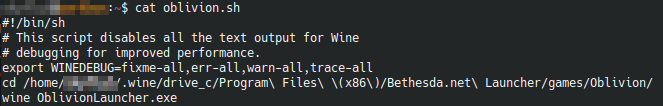
now make sure your script is executable:
chmod +x oblivion.shNow you can launch Oblivion with:
./oblivion.shYou can also use this method to install any of the other games in the Bethesda Launcher library.